So I finally managed to replace my aging ZyXeL ZyWALL 5 firewall with ASA 5505 from Cisco. VirginMedia (again, finally!) doubled my speed from 50 to 100Mbps downsteam and ZeXeL just couldn’t cope. In fact my download, when still having 50Mb/s, was around 30Mb/s anyway due to CPU being maxed out. Amount of LAN to WAN traffic (and vice versa) was simply too much for 266MHz Intel IXP422 CPU.
Anyway my ASA has been with me for some time and I didn’t actually do anything with it until last week. Here is my post from June, 10th 2012 talking about upgrading CF card and RAM. It really has been that long!
I started configuring the device and I have most of my stuff already done apart from one thing that became apparent today – my WAN IP is responding to pings! Not good. Quick command to get it fixed:
icmp deny any outside
Now the command above will deny pings on the OUTSIDE (untrusted) interface. In reality you just knocked off any pings that ASA will allow even on the internal interfaces – to fix this you have to allow ICMP as a protocol in default global policy map. Once done ICMP will be allowed back in (from OUTSIDE to INSIDE) because ASA will “know” about the connection that was made in the first place.
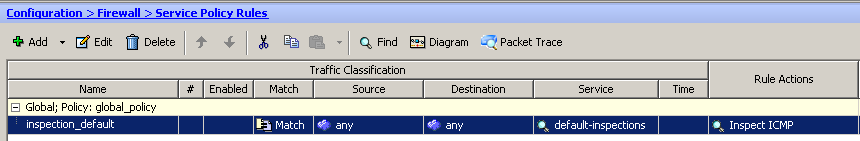
Commands (assuming default policy/inspections name):
policy-map global_policy
class inspection_default
inspect icmp
Like this:
Like Loading...