To cut this long story short – if you have vCenter Server 5.5 update 2 you will have issues if you patch your hosts to the latest available patch level for ESXi. VMware disabled SSLv3 (POODLE and all that..) in update 3b for ESXi meaning if your vCenter Server is running update 2 you won’t be able to connect until the vCenter is patched to update 3b as well. Running ESXi hosts on update 3b and having vCenter Server on update 2 is normally a perfectly valid configuration but because SSLv3 got disabled as part of this process the connectivity is broken.
Example error messages in vpxd log file when patched host in being added to vCenter Server include:
|
1 2 3 4 5 |
2016-02-26T15:47:12.729Z [07448 error 'HttpConnectionPool-000001'] [ConnectComplete] Connect failed to <cs p:0000000017ddfdf0, TCP:spn-esx-04.alex.com:443>; cnx: (null), error: class Vmacore::Ssl::SSLException(SSL Exception: error:140000DB:SSL routines:SSL routines:short read) 2016-02-26T15:47:12.729Z [07400 error 'httphttpUtil' opID=30D532A7-00000053-90] [HttpUtil::ExecuteRequest] Error in sending request - SSL Exception: error:140000DB:SSL routines:SSL routines:short read 2016-02-26T15:47:12.730Z [07400 error 'vpxdvpxdHostAccess' opID=30D532A7-00000053-90] [VpxdHostAccess::Connect] Failed to discover version: vim.fault.HttpFault |
Here’s what VMware has to say about this problem with potential recommendations:
Support for SSLv3 protocol is disabled by default.
In your vSphere environment, you need to update vCenter Server to vCenter Server 5.5 Update 3b before updating ESXi to ESXi 5.5 Update 3b. vCenter Server will not be able to manage ESXi 5.5 Update 3b if you update ESXi before updating vCenter Server to version 5.5 Update 3b. For more information about the sequence in which vSphere environments need to be updated, refer, KB 2057795
VMware highly recommends you to update ESXi hosts to ESXi 5.5 Update 3b while managing them from vCenter Server 5.5 Update 3b.
VMware does not recommend re-enabling SSLv3 due to POODLE vulnerability. If at all you need to enable SSLv3, you need to enable the SSLv3 protocol for all components. For more information, refer KB 2139396.
Now, there will be few scenarios where you cannot upgrade vCenter Server to update 3b or you can’t do so even if its the recommended path and you simply want to have vCenter update 2 working with ESXi update 3b hosts. If fall into this category read on – otherwise update your vCenter! 🙂
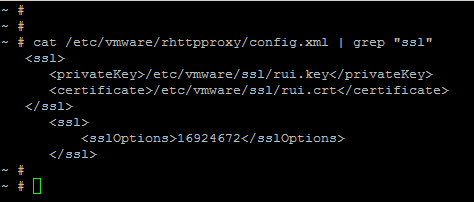
To enable SSLv3 protocol on ESXi update 3b you need to SSH into your host and edit /etc/vmware/rhttpproxy/config.xml with vi and include the following:
|
1 |
<sslOptions>16924672</sslOptions> |
within:
|
1 2 3 4 |
<vmacore><ssl> .. .. </ssl></vmacore> |
tags. Example:
Then save the file and restart the rhttpproxy services by running the following command:
/etc/init.d/rhttpproxy restart
and you should be good to go.
DISCLAIMER:
I’m not saying this solution is what everyone should use and forget about ever disabling SSLv3 protocol but it will certainly get you out of the hot water if you patched X number of hosts and they no longer can connect to vCenter Server. Applying update 3b is the next logical step so drafting plans to have your vCenter Servers upgraded should be on the cards.
Have a good weekend everyone.

Thanks so much! It was exactly the issue I was trying to solve.
Upgraded all vCenter components, problem solved
tried the KB article on VMware’s website and it didn’t work. Tried your article and it worked perfectly
I’m glad it all worked OK for you 🙂
Cheers for this!
when I change the line from
50479104
to
16924672
and I restart the rhttpproxy service, line come to previous value and host is still NOT RESPONDING. 🙁
Should be able to change the configuration to be persistent even across reboots and restarts with the following:
esxcli system settings advanced set -o /UserVars/ESXiRhttpproxyDisabledProtocols -s “”
While the description of where the entry must go, your screenshot showing the context is not accurate. It should look like this:
SNIP
false
true
/lib/
16924672
Apparently the blog comment system strips out anything in brackets, so the above comment is somewhat worthless. Anyway, just pay attention and make sure that the line is within the ssl element *within* the vmacore element, and not near the certificate/privatekey stuff in the section prior to it.