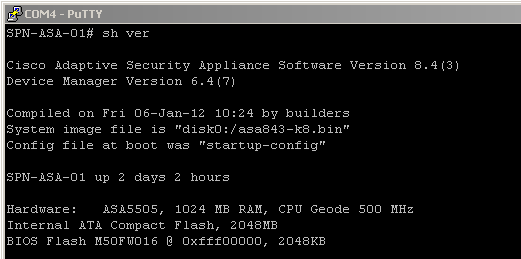
I have had my ASA 5505 running for few months now on Virgin Media FTTN (Fibre To The Neighbourhood / Node) connection and thought I’d share my config. When initial configuration was done on ASA it was a royal pain to be honest, moving from ZyXEL ZyWALL 5 device was challenging since Cisco like to do things differently and ASA is no exception. Here’s what I’m currently running software wise:
ASA software version 8.4.3 and ASDM 6.4.7 – both seem fairly stable so far.
You can safely ignore any defined objects, access lists etc. in the config below as you’d need to re-create them based on what’s required by you.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 |
SPN-ASA-01# sh run : Saved : ASA Version 8.4(3) ! hostname SPN-ASA-01 enable password qWIYV3TAiNmF9uuz encrypted passwd DPqrC7KT9RE36LTW encrypted names ! interface Ethernet0/0 switchport access vlan 100 ! interface Ethernet0/1 switchport access vlan 102 ! interface Ethernet0/2 switchport access vlan 102 ! interface Ethernet0/3 switchport access vlan 101 ! interface Ethernet0/4 switchport access vlan 101 ! interface Ethernet0/5 switchport access vlan 101 ! interface Ethernet0/6 switchport access vlan 101 ! interface Ethernet0/7 switchport access vlan 101 ! interface Vlan100 nameif OUTSIDE security-level 0 ip address dhcp setroute ! interface Vlan101 nameif INSIDE security-level 100 ip address 10.10.0.99 255.255.255.0 ! interface Vlan102 nameif DMZ security-level 50 ip address 10.10.3.1 255.255.255.0 ! boot system disk0:/asa843-k8.bin ftp mode passive object service service_rdp service tcp destination eq 3389 object network rdp_incoming host 10.10.0.5 object network kaplan_wan_incoming host 85.118.9.34 object network http_incoming host 10.10.0.3 object service service_https service tcp destination eq https object service service_http service tcp destination eq www object network https_incoming host 10.10.3.15 object network crashplan_incoming host 10.10.0.3 object service service_crashplan service tcp destination eq 4242 object network myplex_incoming host 10.10.0.3 object service service_myplex service tcp destination eq 32400 access-list OUTSIDE_access_in extended permit tcp any object rdp_incoming eq ftp access-list OUTSIDE_access_in_1 extended permit object service_rdp object kaplan_wan_incoming object rdp_incoming access-list OUTSIDE_access_in_1 extended permit object service_http any object http_incoming access-list OUTSIDE_access_in_1 extended permit object service_https any object https_incoming access-list OUTSIDE_access_in_1 extended permit object service_crashplan any object crashplan_incoming access-list OUTSIDE_access_in_1 extended permit object service_myplex any object myplex_incoming pager lines 24 logging enable logging asdm informational mtu OUTSIDE 1500 mtu INSIDE 1500 mtu DMZ 1500 no failover icmp unreachable rate-limit 1 burst-size 1 icmp deny any OUTSIDE asdm image disk0:/asdm-647.bin no asdm history enable arp timeout 14400 ! object network rdp_incoming nat (INSIDE,OUTSIDE) static interface service tcp 3389 3389 object network http_incoming nat (INSIDE,OUTSIDE) static interface service tcp www www object network https_incoming nat (DMZ,OUTSIDE) static interface service tcp https https object network crashplan_incoming nat (INSIDE,OUTSIDE) static interface service tcp 4242 4242 object network myplex_incoming nat (INSIDE,OUTSIDE) static interface service tcp 32400 32400 ! nat (DMZ,OUTSIDE) after-auto source dynamic any interface description Dynamic PAT for DMZ to OUTSIDE nat (INSIDE,OUTSIDE) after-auto source dynamic any interface description Dynamic PAT for INSIDE to OUTSIDE access-group OUTSIDE_access_in_1 in interface OUTSIDE timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 dynamic-access-policy-record DfltAccessPolicy user-identity default-domain LOCAL aaa authentication ssh console LOCAL http server enable http server idle-timeout 45 http 10.10.0.0 255.255.255.0 INSIDE no snmp-server location no snmp-server contact snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart telnet 10.10.0.0 255.255.255.0 INSIDE telnet timeout 45 ssh 10.10.0.0 255.255.255.0 INSIDE ssh timeout 45 console timeout 0 dhcpd auto_config OUTSIDE ! threat-detection basic-threat threat-detection statistics port threat-detection statistics protocol threat-detection statistics access-list threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200 ntp server 10.10.0.10 source INSIDE webvpn anyconnect-essentials username admin password u7LcBTvp2pgzHGVR encrypted privilege 15 ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect icmp ! service-policy global_policy global prompt hostname context no call-home reporting anonymous call-home profile CiscoTAC-1 no active destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address email callhome@cisco.com destination transport-method http subscribe-to-alert-group diagnostic subscribe-to-alert-group environment subscribe-to-alert-group inventory periodic monthly subscribe-to-alert-group configuration periodic monthly subscribe-to-alert-group telemetry periodic daily SPN-ASA-01# |
Two, arguably, most important lines in the config to get Virgin Media connection going are:
I] Define your untrusted, OUTSIDE interface and set default route to obtain IP address via DHCP:
|
1 2 3 4 5 |
interface Vlan100 nameif OUTSIDE security-level 0 <strong> ip address dhcp setroute</strong> ! |
II] Configure your Dynamic NAT which changed massively in versions > 8.3:
|
1 |
nat (INSIDE,OUTSIDE) after-auto source dynamic any interface description Dynamic PAT for INSIDE to OUTSIDE |
NOTE: If you’re running ASA software prior to 8.3 I’d strongly recommend reading Cisco documentation on changes in NAT as well as checking configuration examples – ASA Pre-8.3 to 8.3 NAT configuration examples
There you have it, ASA 5505 config that works on Virgin Media!
/EDIT
I finally have been given the dreadfull SuperHub from Virgin Media – I have resisted for as long as I possibly could but that’s it – they have taken my belowed modem away now!
I’m pleased to say that once you switch SuperHub to bridge mode it works exectly like my old modem did. Config below works without any modifications which is always good – one thing that drives me mad though is the blue LED light that flashes all the time. Duck tape of bluetac time I think! 🙂

Hi Adrian,
Do you have the Virgin Media 350mbps service? I’m looking at getting the Business service to use with a ASA 5506 and the hitron router that virgin provide in modem mode.
I’m hoping the config you have will work or require small modifications to get it working.
I currently have a asa 5505 on BT infinity which has been working superb for last 4+ years.
Saeed,
What code version are you running on the ASA?
I am currently on 50Mbps VM circuit but will be going up to the 300 one fairly soon albeit not the business one.
The asa 5506 I’ve got has 9.4(1). Virgin will be coming next week to do site survey and do install. In the meantime I need to get a config written so I only have to modify few things when installation goes live.